Should I Log All API Calls? Unpacking the API Logging Question
1. Why even bother with API logging in the first place?
So, you’re wrestling with the question: “Should I log all API calls?” It’s a valid concern, and honestly, there’s no simple yes or no answer. Think of it like deciding whether to document every single detail of your last family vacation. Sure, the memory cards are overflowing with pictures, but do you really need the 47th blurry shot of Aunt Mildred trying to eat a churro? Probably not. But crucial moments? Absolutely! The same principle applies to API calls. We’re talking about recording interactions between different pieces of software, and knowing what to record is key.
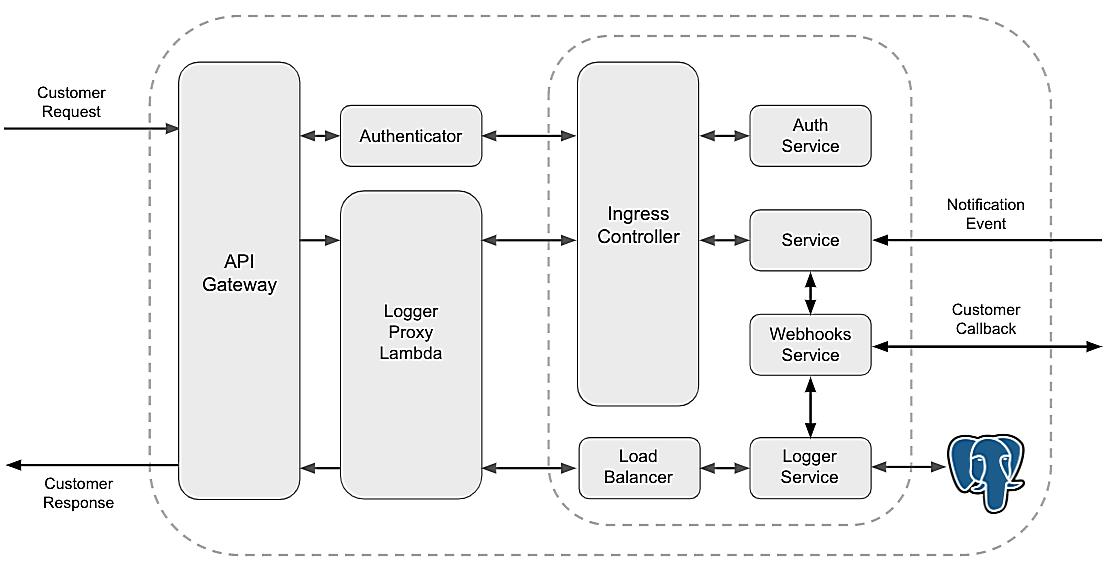
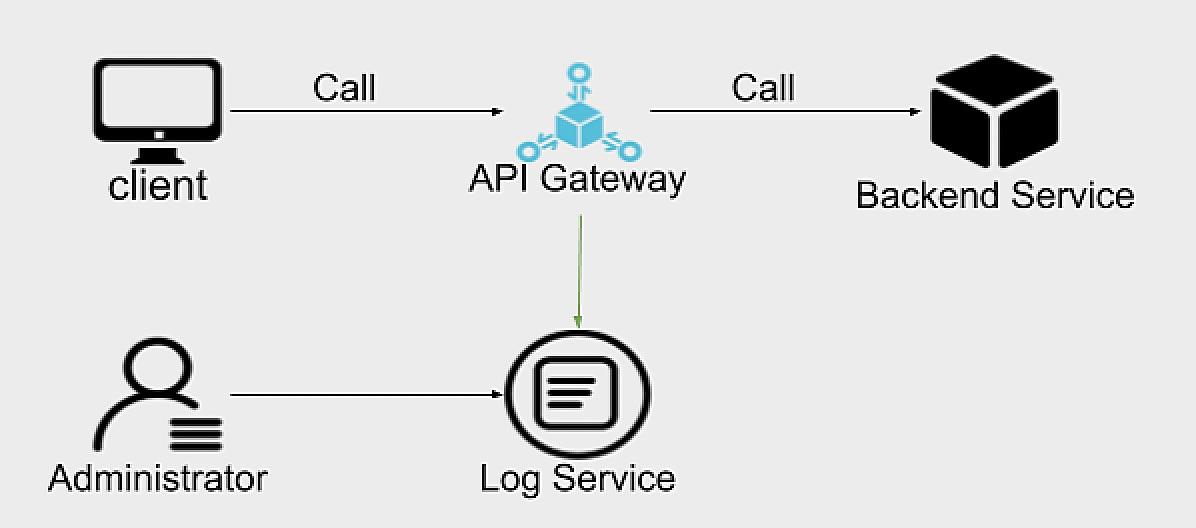
At its core, API logging is about creating a detailed record of communication between applications. Think of it as a flight recorder for your software. When things are running smoothly, it’s just quietly sitting there, but when something goes wrong bam! you’ve got a treasure trove of information to help you figure out what happened. It can be a lifesaver for debugging, security analysis, and just general performance monitoring.
Consider this: imagine your e-commerce website suddenly starts throwing errors during checkout. Customers are abandoning their carts left and right, and the revenue is plummeting faster than a lead balloon. Without API logs, you’re basically stumbling around in the dark, guessing at the root cause. With logs? You can trace the entire transaction, see exactly where the breakdown occurred, and fix it before your boss starts breathing down your neck.
But logging everything? Well, that might be overkill. Just like that family vacation album crammed with duplicates, logging every single API call can lead to a data deluge that’s overwhelming and ultimately unhelpful. So, where’s the sweet spot? Let’s dig a little deeper.
The Upsides
2. The benefits are actually quite significant.
Okay, let’s talk about the good stuff. The advantages of comprehensive API logging are numerous, and they can have a real impact on your software’s performance and your team’s sanity.
First off, debugging becomes a breeze. When an error crops up, you’re not just staring at a cryptic error message. You can actually see the sequence of events that led to the problem. This is incredibly helpful for pinpointing the exact cause and getting a fix in place quickly. Think of it as having a GPS for your code; you can trace your steps back to the starting point.
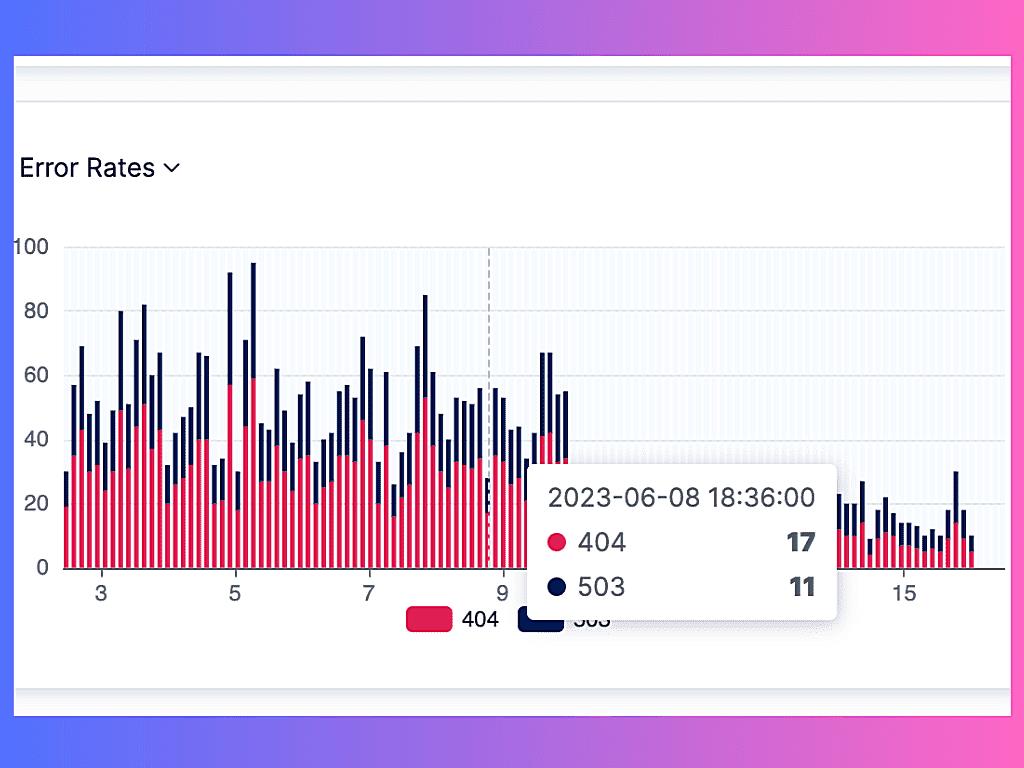
Then there’s security. API logs can be a goldmine for detecting suspicious activity. Unusual patterns, unauthorized access attempts, data breaches — all these can be spotted by analyzing your logs. Its like having a security camera system monitoring your API endpoints.
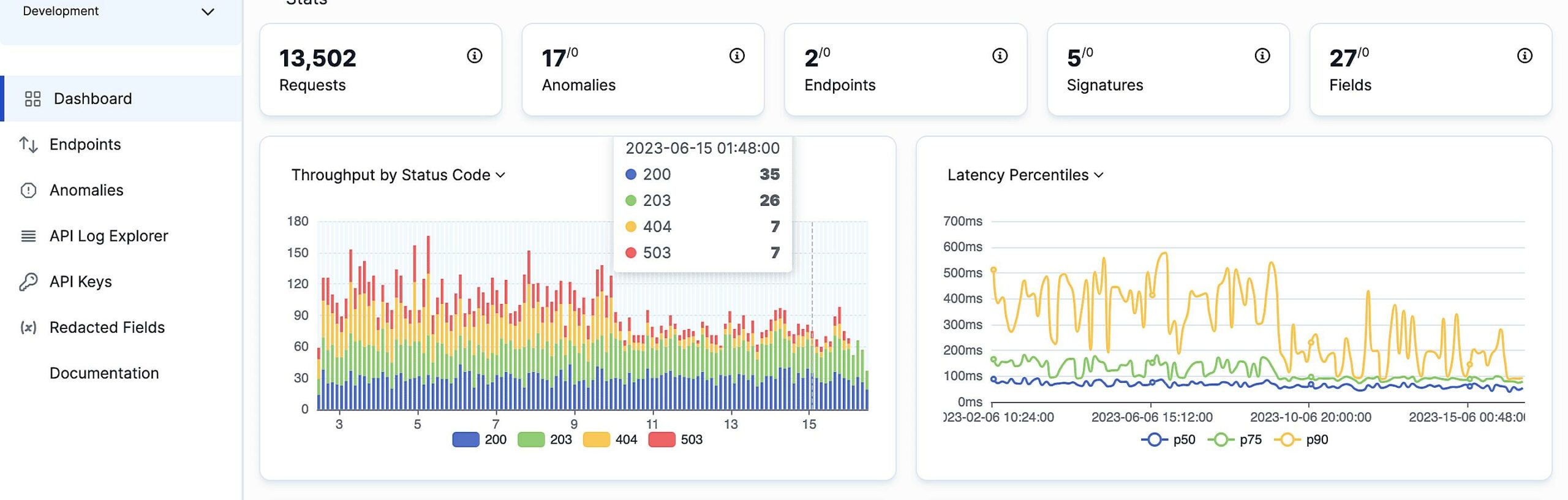
And don’t forget about performance monitoring. Logging response times, request frequencies, and error rates gives you a clear picture of how your APIs are performing under different loads. This allows you to identify bottlenecks, optimize your code, and ensure a smooth user experience. Its like a health check-up for your API, allowing you to identify areas that need attention.
Finally, API logs are invaluable for auditing and compliance. In many industries, you’re required to keep a detailed record of all system activity. API logs provide that record, making it much easier to meet regulatory requirements. Think of it as having all your documents in order before tax season rolls around.
The Downsides
3. Storage costs, performance impacts, and security concerns.
Alright, let’s face the music. Logging everything isn’t all sunshine and rainbows. There are definitely some potential drawbacks to consider.
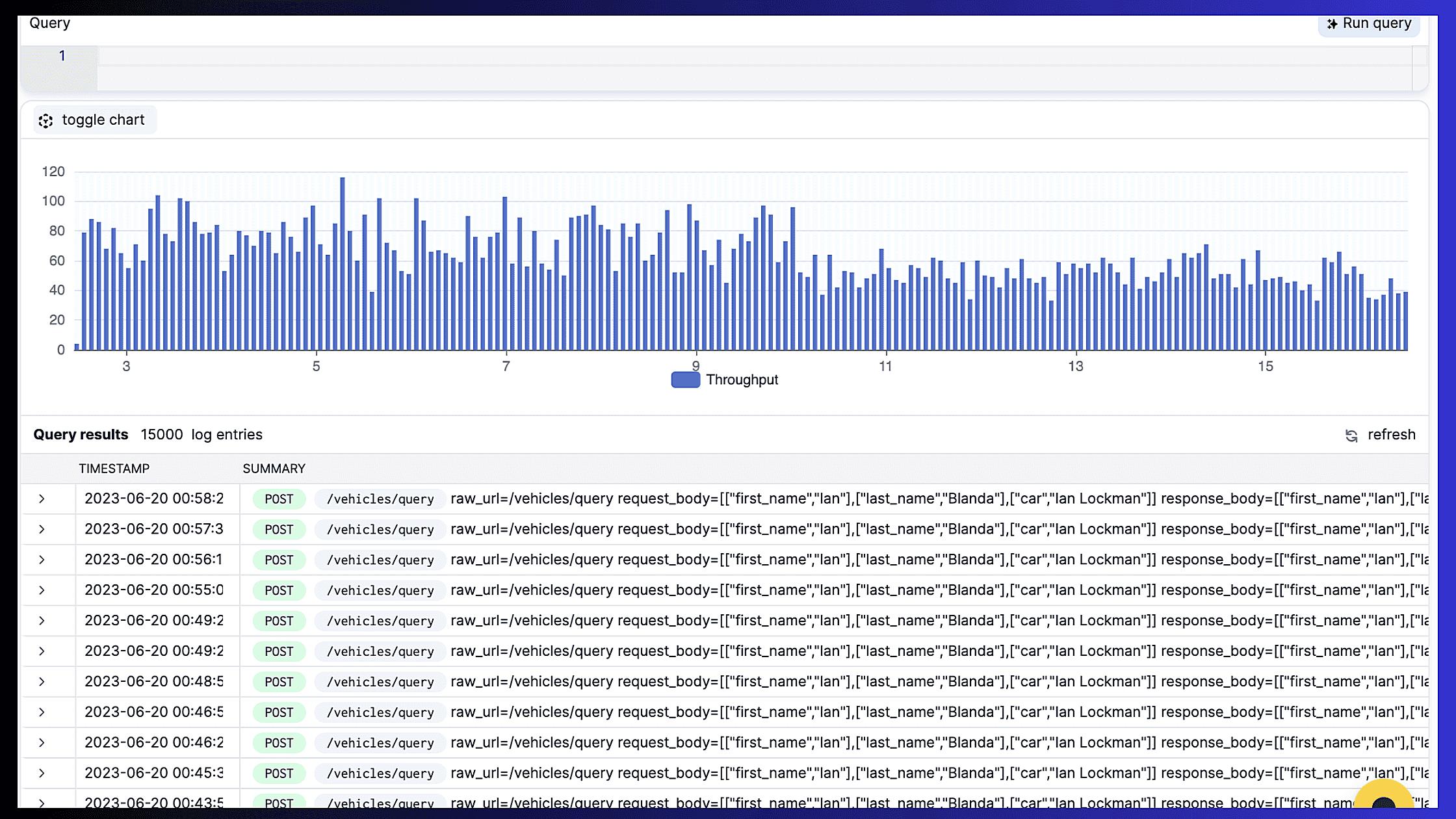
First, there’s the sheer volume of data. Logging every single API call can generate a massive amount of data, especially for high-traffic APIs. This can quickly lead to skyrocketing storage costs. Think of it as trying to store every single grain of sand on a beach — it’s just not practical.
Then there’s the performance impact. Writing logs to disk takes time and resources, which can slow down your APIs, especially under heavy load. This is like adding extra weight to a race car; it might not seem like much at first, but it can make a noticeable difference over time.
And let’s not forget about security risks. API logs often contain sensitive information, such as API keys, user credentials, and personal data. If these logs aren’t properly secured, they can become a juicy target for hackers. Its akin to leaving your house keys under the doormat convenient, but not very secure.
Finally, analyzing and managing large volumes of logs can be a headache. Sifting through mountains of data to find the information you need can be a time-consuming and frustrating process. This is like trying to find a needle in a haystack — possible, but not exactly efficient.
Finding the Balance
4. Prioritizing essential data for meaningful insights.
So, if logging everything is overkill, and logging nothing is irresponsible, what’s the right approach? The key is to be selective and log only the information that’s truly valuable.
Start by focusing on errors and exceptions. These are the red flags that indicate something’s gone wrong. Log the error message, the stack trace, and any relevant context that can help you diagnose the problem. This is like focusing on the warning lights in your car — they’re telling you something important.
Next, consider logging security-related events. This includes authentication attempts, authorization failures, and suspicious activity. These logs can help you detect and prevent security breaches. Its about monitoring your security cameras for any signs of intrusion.
Also, think about logging performance metrics. This includes response times, request frequencies, and resource utilization. These logs can help you identify performance bottlenecks and optimize your code. Keep an eye on your APIs vital signs.
Finally, be sure to log important business transactions. This could include orders placed, payments processed, or data updates. These logs can be invaluable for auditing and reporting. Its like keeping a detailed ledger of all your business transactions.
Tools and Techniques
5. Implementing efficient and secure logging practices.
Okay, you’ve decided what to log. Now, how do you actually do it? Fortunately, there are plenty of tools and techniques to make API logging easier and more efficient.
First, choose a logging framework. There are many popular logging frameworks available, such as Log4j, SLF4J, and Winston. These frameworks provide a standardized way to log messages, making it easier to manage and analyze your logs. Think of it as using a common language for all your applications.
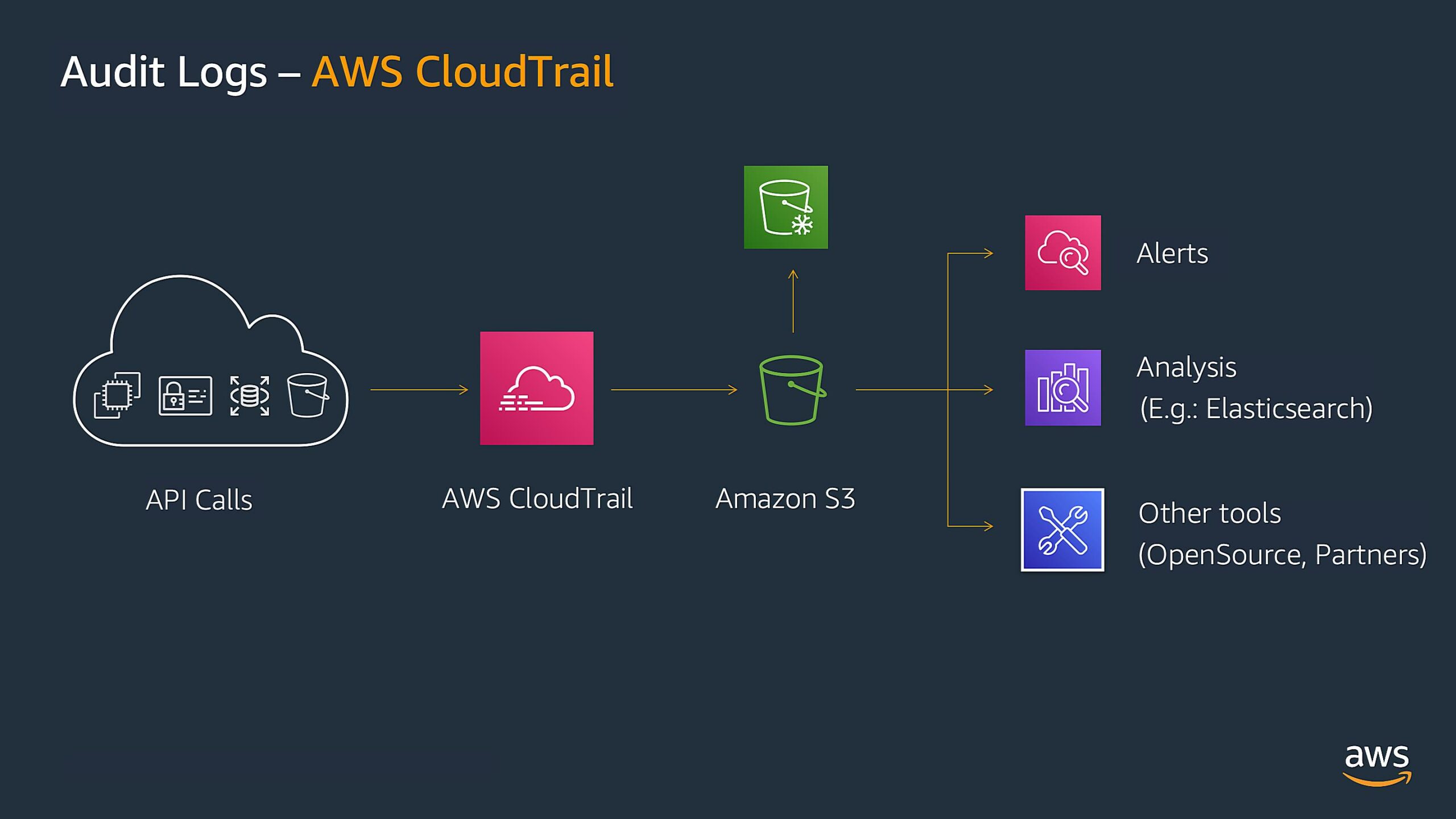
Then, use a centralized logging system. This allows you to collect logs from multiple servers and applications in one place. Popular centralized logging systems include the ELK stack (Elasticsearch, Logstash, Kibana) and Splunk. It’s like having a single dashboard for monitoring all your systems.
Also, encrypt your logs. Since API logs often contain sensitive information, it’s crucial to encrypt them to protect them from unauthorized access. This is like locking up your valuables in a safe.
Finally, rotate your logs. Over time, log files can grow very large, making them difficult to manage. Rotating your logs involves archiving old log files and starting new ones. This helps to keep your log files manageable and prevents them from consuming too much disk space. Think of it as cleaning out your closet every so often.
FAQ
6. Q
A: Logging is about recording individual events, while monitoring is about tracking overall system performance. Logs provide detailed information about what happened, while monitoring provides a high-level overview of how things are performing. Think of logging as taking notes during a meeting, and monitoring as watching the meeting from a distance.
7. Q
A: That depends on your regulatory requirements and your business needs. Some industries require you to keep logs for several years, while others only require you to keep them for a few months. Consider the potential value of the logs for auditing, security analysis, and debugging when making your decision. Theres no one-size-fits-all answer.
8. Q
A: Encrypt your logs, store them in a secure location, restrict access to authorized personnel only, and regularly audit your logging system. Think of it as protecting any other sensitive data; apply layers of security.